Mobile apps have become a ubiquitous feature of the modern lifestyle: whether they’re keeping up with friends and family throughout the day, pausing for a round of Candy Crush, or obsessively tapping social media notifications from dawn til dusk, Americans now spend 90% of their online life within the confines of an app. However, very few users or developers are aware of the dangers that this mobile activity regularly exposes them to.
It’s no secret that mobile apps represent a security risk, especially in terms of data privacy. As far back as 2013, a majority of smartphone owners were at least somewhat worried about this, and particularly egregious examples of data privacy abuse such as the recent FaceApp scandal have generated enough buzz to penetrate the mainstream media.
However, major app stores and developers understand the negative perception they are subject to, assuring users that the data they collect is for legitimate purposes. Eventually, users are lulled into a false sense of security by opt-in prompts which require user consent before an app can access their contacts, location, calls, or keystrokes.
Unfortunately, this sense of security stems from a dangerous misconception: in the vast majority of cases, app developers are not the only parties with access to data generated by users. When they grant permissions to a seemingly trustworthy app, users are unwittingly exposing their personal information to dozens of potentially malicious or compromised third-parties.
Third-Party Code Explained
When developers build websites or mobile apps, they rarely start from scratch: third-party vendors provide the code required for a variety of complex functions and dependencies from payment processing to page rendering and – most importantly – programmatic advertising. Although third-party code (or 3PC) is an essential part of the modern digital ecosystem, it is often an attack surface for bad actors.
Today, 3PC is the biggest driver of malware across the web, and it has quickly adapted to take advantage of mobile applications. Through third-party dependencies, malicious actors can drop persistent tracking cookies which spy on users and siphon personal information – including keystrokes, location data and more – back to its source.
Mobile 3PC: The Scale of the Problem
Over the years, sections of the mobile app market have developed different reputations for security. Users and developers alike tend to assume, for instance, that Android devices are more susceptible to malicious code hidden in apps than iOS devices. Our research challenges this assumption, revealing that 9 out 10 apps in the iOS store contained 3PC.
Additionally, we found that:
- On average, 13 third parties had access to user data during installation
- 23 third parties had access during in-app purchases
- 90% of network calls across top performing apps were made to third parties
- 67% of cookies dropped by third parties are persistent, with an average lifespan of 1.5 years
Predictably, the largest single source of 3PC included advertiser and AdTech code powering display, banner and pop-up advertisements from within the application. Other sources included ISP and hosting infrastructure, publishers and – most concerningly – suspicious or unidentifiable third parties.
A break-down follows:
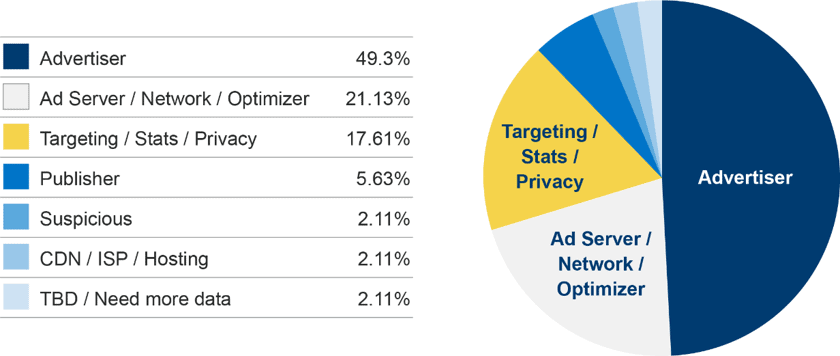
Although suspicious and unknown sources accounted for only 5% of the cookies present, they are not the only ones susceptible to manipulation by bad actors: ad networks, for instance, are frequently targeted by ‘malvertisers’. In October of last year, both Apple and Google purged 50 apps from their mobile stores for serving infected ads to users, showing that 3PC associated with AdTech is not automatically innocuous.
The Risks of Mobile 3PC
For mobile users, the risk presented by 3PC is extensive: not only can it compromise their location, identity and typing history, but it may also lead to malware, phishing or man-in-the-middle attacks that steal credit card information through their browser or mobile wallets. One instance of this attack style includes the PayLeak-3PC incident which impacted countless iOS and Android users in 2018.
For publishers and app developers, 3PC represents a threat to user trust, and – more seriously – may violate emerging data privacy legislation which requires publishers to seek consent from users before allowing third-party access to their data and to actively monitor the way vendors use this information. As the U.S takes the proposition of national data privacy laws seriously, it is high time for developers to take their third-parties seriously as well.
Bottom line: users must be cautious about installing apps from unknown developers. They should also be aware that even trusted developers depend on 3PC, and – as of January 2020 – very few developers are monitoring third parties for suspicious activities. For developers, this research should be a wake-up call to vet dependencies used in app development and invest in resources to keep their users’ data safe.


